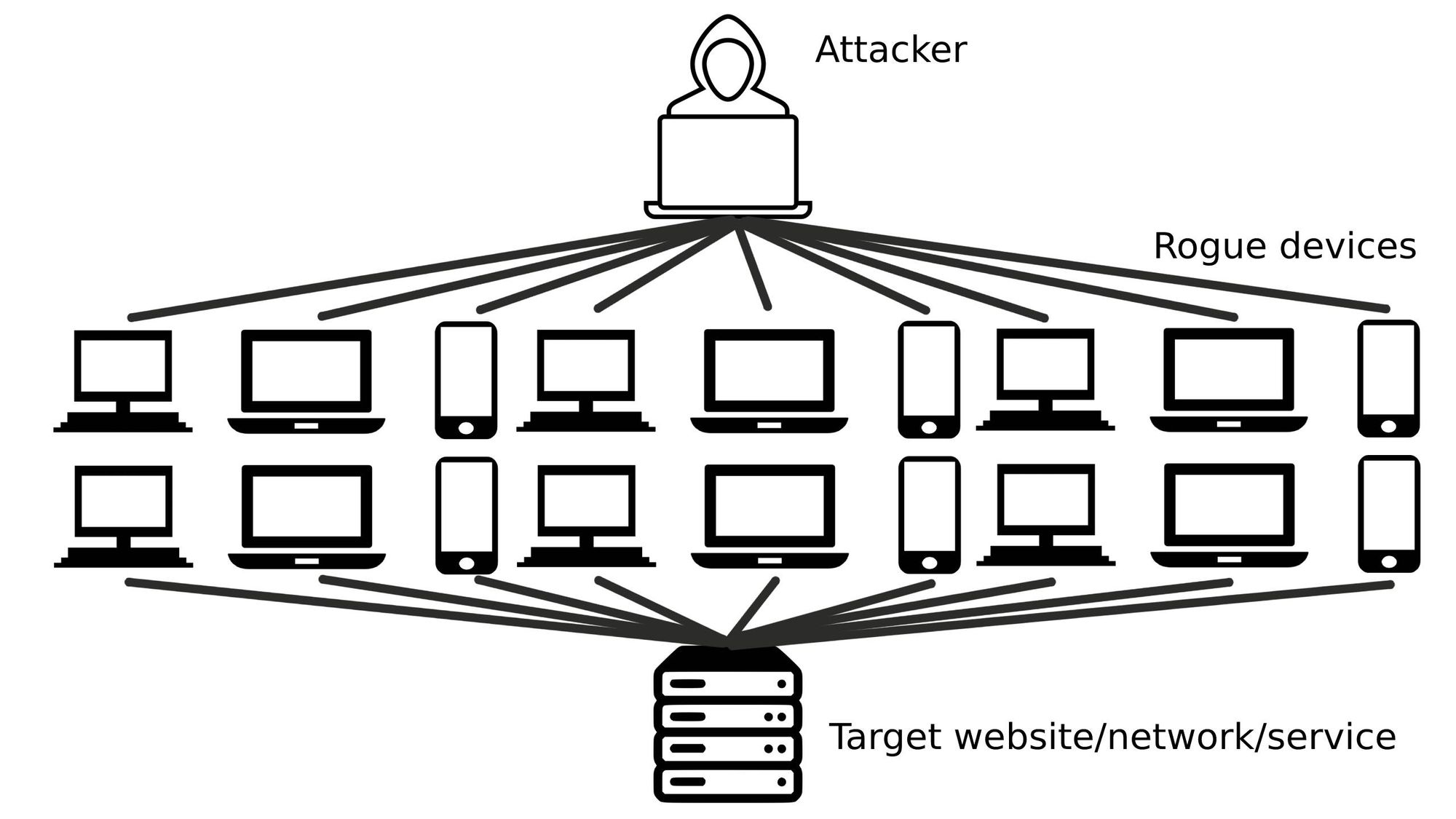
Cloudflare claims pro-Russian hacktivist groups launched DDoS attacks on Australian organizations | Digital Watch Observatory
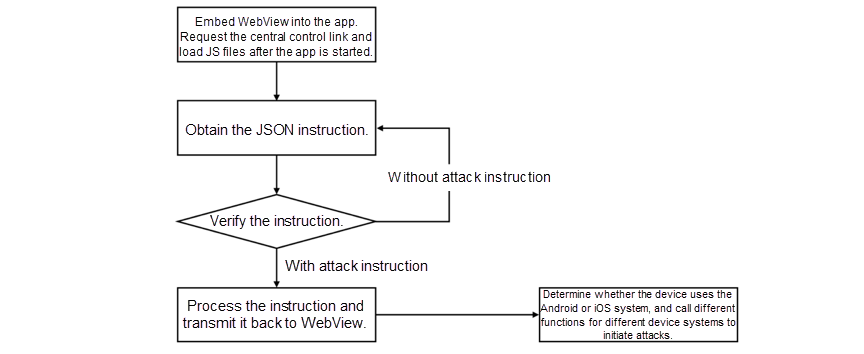
A New Trend of DDoS Attacks: Mobile Devices Are Becoming a New Generation of Botnets - Alibaba Cloud Community
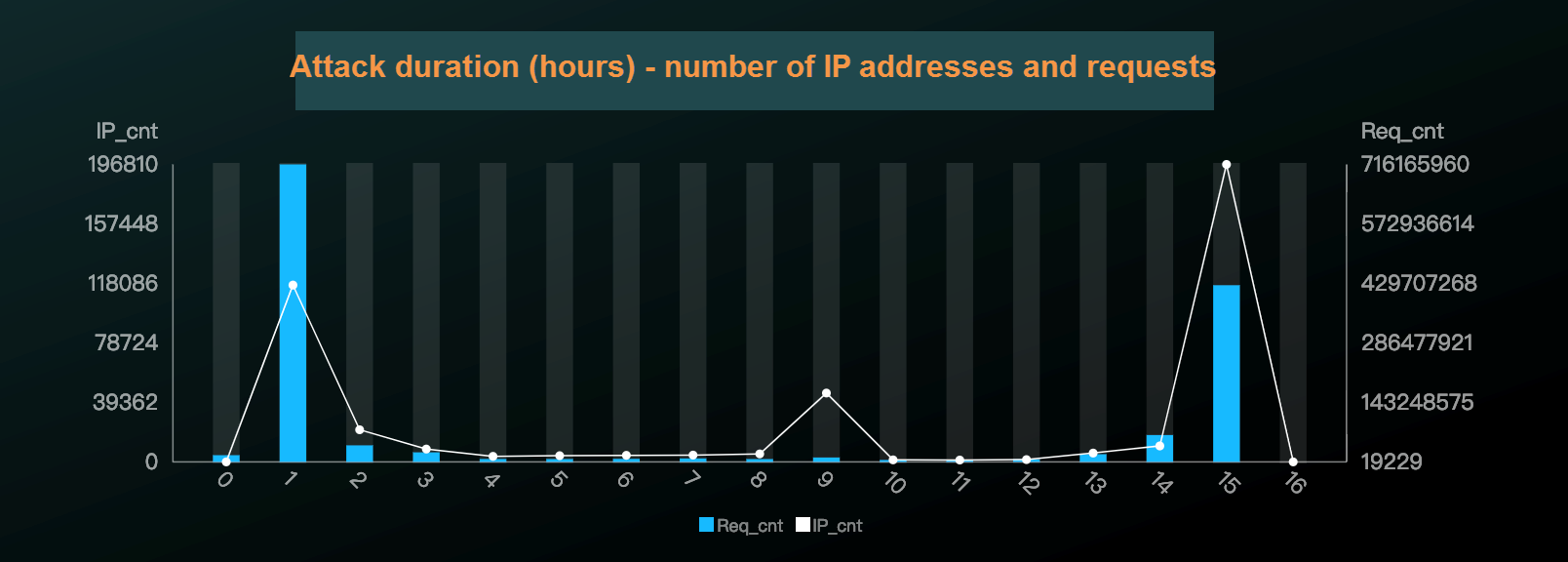
A New Trend of DDoS Attacks: Mobile Devices Are Becoming a New Generation of Botnets - Alibaba Cloud Community
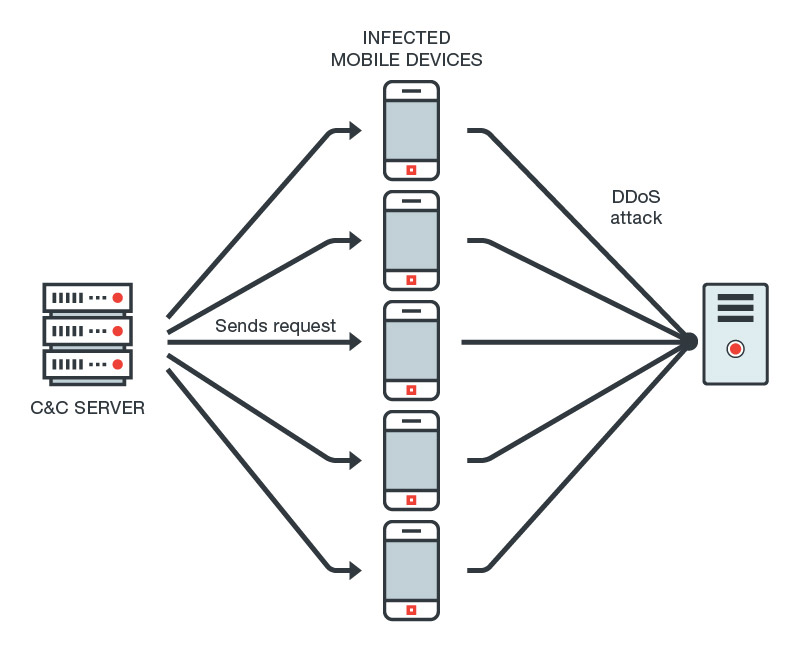
Sockbot Malware Found on Google Play can Ensnare Devices to Become Part of a DDoS Botnet - Wiadomości bezpieczeństwa